How does Gooligan Malware work and which are the infected apps ? Edited by viki4vikram at 2016-12-04 12:10
How does Gooligan work? The infection begins when a user downloads and installs a Gooligan-infected app on a vulnerable Android device. Research team has found infected apps on third-party app stores, but they could also be downloaded by Android users directly by tapping malicious links in phishing attack messages. After an infected app is installed, it sends data about the device to the campaign’s Command and Control (C&C) server. Gooligan then downloads a rootkit from the C&C server that takes advantage of multiple Android 4 and 5 exploits including the well-known VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153). These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user. If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely. After achieving root access, Gooligan downloads a new, malicious module from the C&C server and installs it on the infected device. This module injects code into running Google Play or GMS (Google Mobile Services) to mimic user behavior so Gooligan can avoid detection, a technique first seen with the mobile malware HummingBad. The module allows Gooligan to:
Ad servers, which don’t know whether an app using its service is malicious or not, send Gooligan the names of the apps to download from Google Play. After an app is installed, the ad service pays the attacker. Then the malware leaves a positive review and a high rating on Google Play using content it receives from the C&C server. Research team was able to identify several instances of this activity by cross-referencing data from breached devices with Google Play app reviews. This is another reminder of why users shouldn’t rely on ratings alone to decide whether to trust an app. Goo4 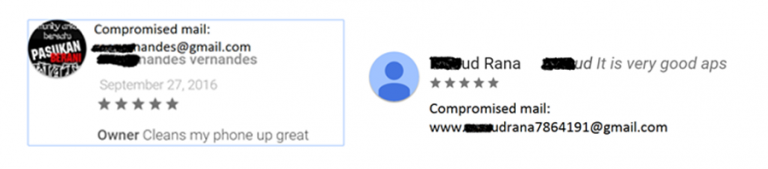
Two examples of reviews left by users who were also found on the attacker’s records as victims. Goo5 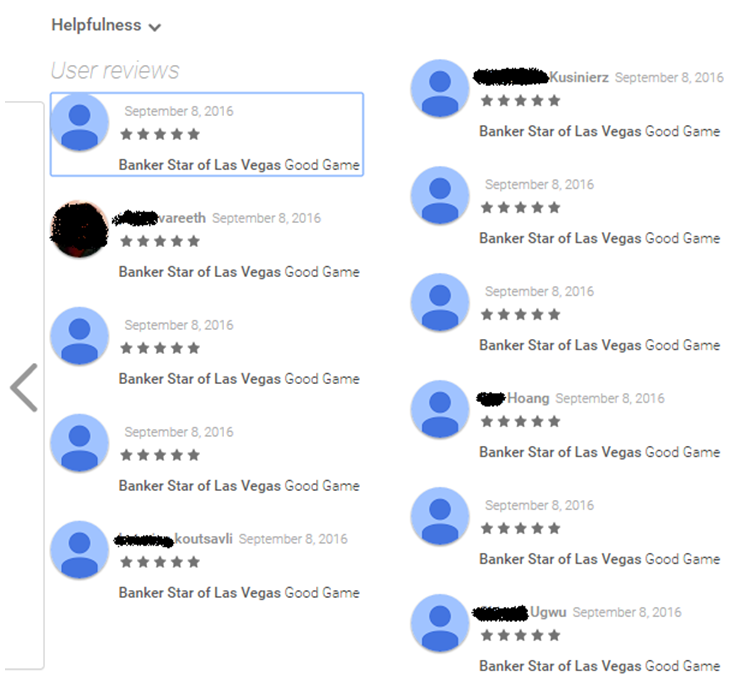
An example of fake reviews and comments to one of the fraudulent applications. Goo6 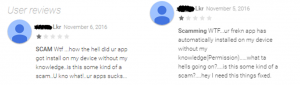
The same user discovered two different fraudulent apps were installed on his device, without his knowledge. Similar to HummingBad, the malware also fakes device identification information, such as IMEI and IMSI, to download an app twice while seeming like the installation is happening on a different device, thereby doubling the potential revenue. Goo7 
One of the apps downloaded from Google Play by Gooligan. What are Google authorization tokens? A Google authorization token is a way to access the Google account and the related services of a user. It is issued by Google once a user successfully logged into this account. When an authorization token is stolen by a hacker, they can use this token to access all the Google services related to the user, including Google Play, Gmail, Google Docs, Google Drive, and Google Photos. While Google implemented multiple mechanisms, like two-factor-authentication, to prevent hackers from compromising Google accounts, a stolen authorization token bypasses this mechanism and allows hackers the desired access as the user is perceived as already logged in. Conclusion Gooligan has breached over a million Google accounts. It is believed that this is the largest Google account breach to date. List of fake apps infected by Gooligan :
More details here Source - Checkpoint | |
|
|
|





























0